The case of Apple vs FBI has drawn attention to the issue of privacy, particularly in the context of mobile devices. After the San Bernardino terrorist attack in 2015, the FBI seized a cell phone belonging to the shooter, Syed Farook, with the intent to search for additional evidence or clues relating to the ongoing investigation. However, despite being in possession of the device, the FBI was unable to unlock the phone and access its contents.
This may seem disconcerting at first.
"Surely if the FBI had access to the phone, they couldn't extract user data stored on it using forensic tools?"
Well, the answer isn't that simple. You see, the device in question is an iPhone 5c with iOS 9.
As you know, starting with iOS 8, Apple has automatically activated the Full Disk Encryption (FDE) using an encryption key derived from the user's password. To access the data on the device, the FBI would have to break that encryption. Barring any errors in the encryption design, this would most likely have been achieved by cracking the user's password.
"So why not use brute-forcing?"
This sounds like a very good approach - especially since most users are notoriously clumsy in choosing strong passwords, even more so when it comes to mobile devices.
However, Apple's engineers were not unaware of this concern when they designed their FDE scheme. In order to try to mitigate this type of attack, they designed the encryption scheme so that the generated cryptographic key is tied to the device hardware.
In short, each device has a unique 256-bit immutable key called UID, which is generated randomly and merged into the device hardware when it is produced. The key is stored in a way that completely prevents access using software or firmware (it can only be set as a key for the AES engine), which means that not even Apple can pull it out of the device once it has been set up.
This device-specific key is then used in conjunction with the user-supplied password to generate the resulting encryption key used to protect device data. This effectively "tangles" the password and UID key.
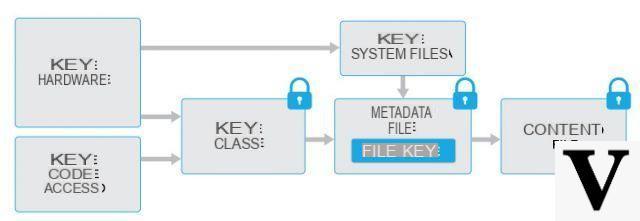
Binding the encryption key to the device's hardware allows Apple to make work that much more difficult for potential attackers. Essentially it forces attackers to use the device for every attempted breach. This, in turn, allows Apple to introduce a whole host of defenses that would make hacking attempts inconvenient.
To begin with, the key derivation function is designed in such a way that it would take a significant amount of time to calculate it on the device. Specifically, Apple chose function parameters so that a single derivation key would have a delay of approximately 80 milliseconds. This delay would make hacking of short alphanumeric passwords slow (about 2 weeks for a 4-character alphanumeric password), and hacking longer passwords completely unworkable.
In order to further mitigate brute-force attacks on the device itself, Apple has also introduced an incremental delay between successive password guessing attempts. On the iPhone 5c, this delay was eased completely via software. Finally, Apple has allowed the ability to completely erase all data stored on the device after 10 failed attempts to retrieve the password. This setup, coupled with software-induced delays, made hacking the password on the device itself rather impractical.
DELAY BETWEEN ATTEMPTS
- [1-4]> None
- [5]> 1 Minute
- [6]> 5 Minutes
- [7-8]> 15 minutes
- [9]> 1 hour
Knowing this, it is much more reasonable to assume that the FBI was unable to crack the device's encryption.
If they had been able to extract the UID key, they could have used the necessary (specialized) hardware, in order to quickly find many passwords, which would likely have allowed them to find the correct password. However, since the UID key cannot be extracted via software or firmware, this option is excluded.
As for hacking the password on the device, software-induced delays between password entry attempts and the ability to delete all data on the device made the option not very convenient. This excludes the possibility of bypassing the software protections.
Returning to the question at hand - we can see that Apple has cleverly designed its FDE scheme in a way that makes it very difficult to crack.
by