- Our video
- What is a firewall?
- How a firewall system works
- Personal firewall concept
- The limits of firewalls
- To download
Our video
Loading your "FAQ: Firewall" videoEvery computer connected to the Internet (and more generally to any computer network) is susceptible to an attack by a hacker. The methodology generally employed by the hacker is to scan the network (by sending data packets in a random fashion) for a connected machine, then to look for a security vulnerability in order to exploit it and access the data. data therein.
This threat is all the greater since the machine is permanently connected to the internet for several reasons:
- The target machine is likely to be connected without being monitored;
- The target machine is generally connected with a higher bandwidth;
- The target machine does not change (or little) IP address.
Thus, it is necessary, both for business networks and for Internet users who have a cable or ADSL type connection, to protect themselves from network intrusions by installing a protection device.
What is a firewall?
Un firewall (also called firebreak, gatekeeper or firewall in English), is a system allowing to protect a computer or a network of computers from intrusions coming from a third network (in particular Internet). The firewall is a system making it possible to filter the data packets exchanged with the network, it is thus a filtering gateway comprising at least the following network interfaces:
- an interface for the network to be protected (internal network);
- an interface for the external network.
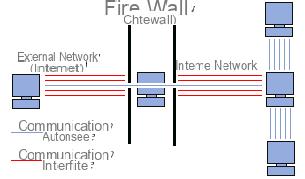
The firewall system is a software system, sometimes based on dedicated network hardware, constituting an intermediary between the local network (or the local machine) and one or more external networks. It is possible to put a firewall system on any machine and with any system provided that:
- The machine is powerful enough to handle the traffic;
- The system is secure;
- No service other than the packet filtering service is running on the server.
In the event that the firewall system is supplied in a “turnkey” black box, the term “appliance” is used.
How a firewall system works
A firewall system contains a set of predefined rules allowing:
- To authorize the connection (allow);
- To block the connection (deny);
- To reject the connection request without notifying the sender (drop).
All of these rules make it possible to implement a filtering method depending on the security policy adopted by the entity. There are usually two types of security policies allowing:
- either to authorize only communications that have been explicitly authorized (this is the principle of least privilege);
- or to prevent exchanges that have been explicitly prohibited.
The first method is undoubtedly the safest, but it nevertheless imposes a precise and restrictive definition of communication needs.
Simple packet filtering
A firewall system operates on the principle of simple packet filtering (in English "stateless packet filtering"). It analyzes the headers of each data packet (datagram) exchanged between a machine on the internal network and an external machine.
Thus, the data packets exchanged between a machine on the external network and a machine on the internal network pass through the firewall and have the following headers, systematically analyzed by the firewall:
- IP address of the sending machine;
- IP address of the receiving machine;
- type de paquet (TCP, UDP, etc.) ;
- port number (reminder: a port is a number associated with a network service or application).
The IP addresses contained in the packets identify the sending machine and the target machine, while the type of packet and the port number give an indication of the type of service used.
The table below gives examples of firewall rules:
| Rule | Action | Source IP | IP dest | Protocol | Source port | Port dest |
|---|---|---|---|---|---|---|
| 1 | Accept | 192.168.10.20 | 194.154.192.3 | tcp | Any | 25 |
| 2 | Accept | Any | 192.168.10.3 | tcp | Any | 80 |
| 3 | Accept | 192.168.10.0/24 | Any | tcp | Any | 80 |
| 4 | Deny | Any | Any | Any | Any | Any |
The recognized ports (whose number is between 0 and 1023) are associated with current services (ports 25 and 110 are for example associated with electronic mail, and port 80 with the Web). At a minimum, most firewall devices are configured to filter communications according to the port used. It is generally advisable to block all the ports which are not essential (according to the chosen security policy).
Port 23 is for example often blocked by default by firewall devices because it corresponds to the Telnet protocol, making it possible to emulate terminal access to a remote machine so as to be able to execute commands remotely. The data exchanged by Telnet is not encrypted, which means that an individual is likely to listen to the network and to steal any passwords circulating in the clear. Administrators generally prefer the SSH protocol, which is known to be secure and provides the same functionality as Telnet.
Dynamic filtering
Simple packet filtering focuses only on examining IP packets independently of each other, which corresponds to level 3 of the OSI model. However, most connections are based on the TCP protocol, which manages the notion of session, in order to ensure the smooth running of the exchanges. On the other hand, many services (FTP for example) initiate a connection on a static port, but dynamically (i.e. randomly) open a port in order to establish a session between the machine acting as server and client machine.
Thus, it is impossible with simple packet filtering to predict which ports to pass or to deny. To remedy this, the dynamic packet filtering is based on the inspection of layers 3 and 4 of the OSI model, allowing the tracking of transactions between the client and the server. The Anglo-Saxon term is " stateful inspection Or "stateful packet filtering", translate "stateful packet filtering".
A “stateful inspection” type firewall device is thus capable of monitoring exchanges, that is to say of taking into account the state of old packets in order to apply the filtering rules. In this way, from the moment an authorized machine initiates a connection to a machine located on the other side of the firewall; all the packets passing through this connection will be implicitly accepted by the firewall.
While dynamic filtering is more efficient than basic packet filtering, it does not, however, protect against the exploitation of application flaws, linked to application vulnerabilities. However, these vulnerabilities represent the most important part of the risks in terms of security.
Application filtering
Application filtering allows you to filter communications application by application. Application filtering therefore operates at level 7 (application layer) of the OSI model, unlike simple packet filtering (level 4). Application filtering therefore assumes knowledge of the protocols used by each application.
Application filtering makes it possible, as its name suggests, to filter communications application by application. Application filtering therefore assumes a good knowledge of the applications present on the network, and in particular of the way in which it structures the data exchanged (ports, etc.).
A firewall performing application filtering is generally called an “application gateway” (or “proxy”), because it acts as a relay between two networks by interposing and performing fine validation of the content of the packets exchanged. The proxy therefore represents an intermediary between the machines of the internal network and the external network, undergoing attacks in their place. In addition, application filtering allows the destruction of the headers preceding the application message, which makes it possible to provide an additional level of security.
It is a powerful device, ensuring good protection of the network, as long as it is properly administered. On the other hand, a detailed analysis of the application data requires a great deal of computing power and therefore often results in slower communications, each packet having to be finely analyzed.
In addition, the proxy must necessarily be able to interpret a wide range of protocols and know the related flaws to be effective.
Finally, such a system can potentially have a vulnerability insofar as it interprets the requests that pass through it. Thus, it is recommended to dissociate the firewall (dynamic or not) from the proxy, in order to limit the risk of compromise.
Personal firewall concept
If the protected zone is limited to the computer on which the firewall is installed, we speak of firewall personnel (personal firewall).
Thus, a personal firewall makes it possible to control the access to the network of the applications installed on the machine, and in particular to prevent attacks of the Trojan horse type, that is to say harmful programs opening a breach in the system in order to allow a hacker to take control of the machine remotely. The personal firewall makes it possible to identify and prevent unsolicited opening by unauthorized applications.
The limits of firewalls
A firewall system obviously does not offer absolute security, on the contrary. Firewalls only offer protection to the extent that all communications to the outside world systematically pass through them and that they are correctly configured. Thus, access to the external network by bypassing the firewall are all security vulnerabilities. This is particularly the case for connections made from the internal network using a modem or any means of connection beyond the control of the firewall.
Likewise, the introduction of storage media from outside on machines internal to the network or on laptops can seriously damage the overall security policy.
Finally, in order to guarantee a maximum level of protection, it is necessary to administer the firewall and in particular to monitor its activity log in order to be able to detect intrusion attempts and anomalies. In addition, it is recommended to carry out a security watch (by subscribing to security alerts from CERTs for example) in order to modify the configuration of your device according to the publication of the alerts.
The installation of a firewall must therefore be done in accordance with a real security policy.
To download
- Download / Firewall: ZoneAlarm, Comodo Firewall, etc.
- Antivirus gratuit : Antivir, Avast, AVG, Bitdefender, Microsoft Security Essentials, etc.