Our video
Loading your "FAQ: Electronic signature" videoIntroduction to the concept of electronic signature
The paradigm of electronic signature (also called digital signature) is a process
to guarantee the authenticity of the sender (function
authentication) and check the integrity of the message received.
The electronic signature also ensures a non-repudiation function,
that is to say, it ensures that the sender has sent the message (in other words, it prevents
the sender to deny having sent the message).
What is a hash function?
A hash function (sometimes called the condensation function) is a function
allowing to obtain a condensate (also called condensate or chopped or in English
digest message) of a text,
i.e. a fairly short series of characters representing the text that
condenses. The hash function must be such that it associates one and only one hash with a plaintext
(this means that the slightest modification of the document results in the modification of its hash).
On the other hand, it must be a one-way function so that it is
impossible to find the original message from the digest.
If there is a way to retrieve the plaintext message from the hash, the hash function
is said to be “a secret breach”.
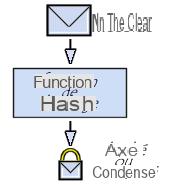
So the hash sort of represents the fingerprint
(in English finger print) of the document.
The most used hashing algorithms currently are:
- MD5 (MD meaning Message Digest).
Developed by Rivest in 1991, MD5 creates a fingerprint
128 bits from a text of size
arbitrary by processing it in blocks of 512 bits. It is common to see
documents for downloading from the Internet accompanied by an MD5 file, this is the summary
of the document making it possible to verify the integrity of the latter)
- SHA (for Secure Hash Algorithm, translatable as Secure Hash Algorithm) creates
160-bit long hash SHA-1 is an improved version of SHA dating from 1994 and producing a 160-bit hash
from a message with a maximum length of 264 bits by processing it with
512-bit blocks.
Integrity check
By sending a message accompanied by its hash, it is possible
to guarantee the integrity of a message, that is to say that the recipient
can verify that the message has not been tampered with (intentionally or
accidentally) during the call.
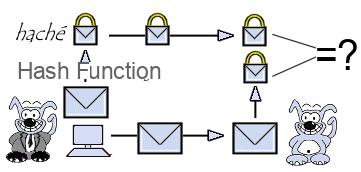
When receiving the message, the recipient just has to calculate the hash of the received message and
compare it with the hash accompanying the document. If the message (or the hash) has been tampered with
during communication, the two fingerprints will not match.
Data sealing
Using a hash function verifies that the fingerprint matches the message.
received, but nothing proves that the message was sent by the one we believe
be the sender.
Thus, to guarantee the authentication of the message, it is sufficient for the sender to encrypt (we generally say to sign) the digest.
using its private key (the signed hash is called seal) and send the seal to the recipient.
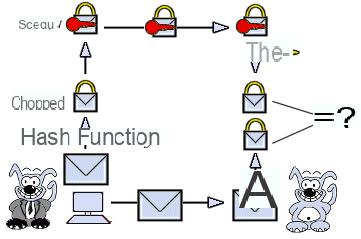
Upon receipt of the message, the recipient simply has to decipher the seal with the key.
sender's public, then compare the hash obtained with the hash function to the hash received
as an attachment. This sealing mechanism is called sealing.
+ Info
- SHA1 Secure Hash Algorithm - Version 1.0
- RFC 3174 (rfc3174) - US Secure Hash Algorithm 1 (SHA1)
- RFC 1321 (rfc1321) - The MD5 Message-Digest Algorithm













![[Review] Samsung Powerbot VR7000: the robot vacuum cleaner from Star Wars](/images/posts/6bc44de38605b5c0fa12661febb1f8af-0.jpg)